A Roadmap for Next Generation Biometric Template Protection
Martigny Biometrics Workshop
Vishnu Boddeti
Michigan State University & Suraksh AI
Biometric Systems are vulnerable to many attacks












Template-Based Attacks

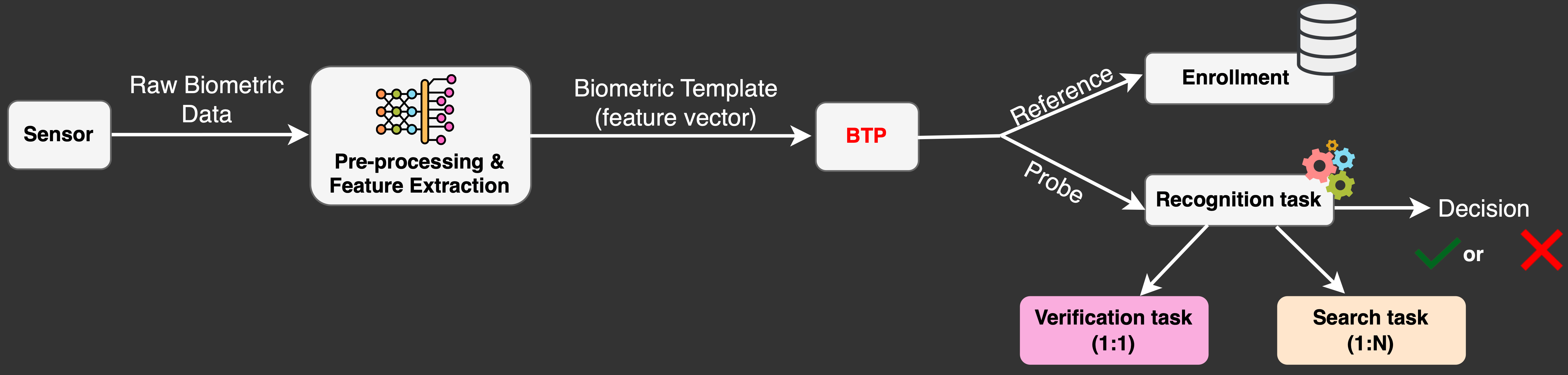
Biometric Template Protection
- Goal: Protecting templates in a biometric system.
- Conceptual idea of BTP:
- Template -> Transform -> Protected Template
Categories of BTP Methods
Hand-Designed Feature Transforms
Learned Feature Transforms
Homomorphic Encryption
Biometric Cryptosystems
Today's Agenda
Next Generation of BTP Methods
Privacy and Security for biometric recognition


There is no privacy without security
Categorizing BTP Methods
Hand-Designed Feature Transforms
Learned Feature Transforms
Homomorphic Encryption
Biometric Cryptosystems
Hybrid BTP with Privacy and Security
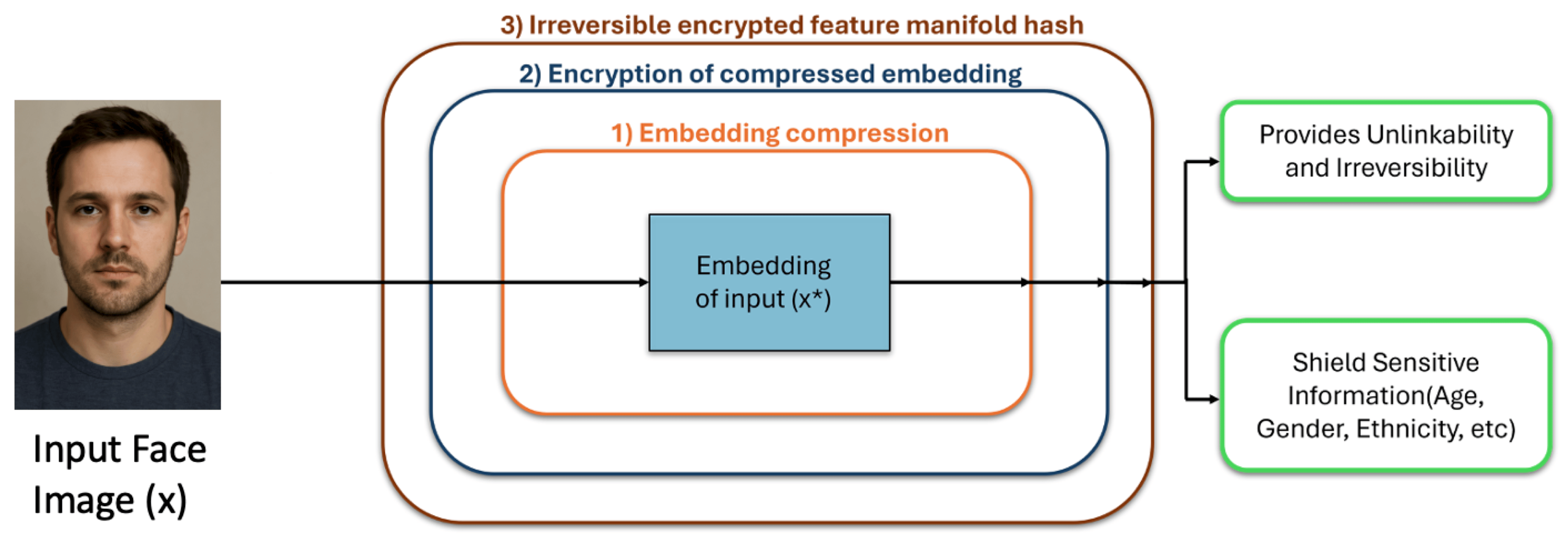
Next Generation of BTP Methods
Protection Offered by BTP Schemes
- Depends on the intrinsic dimensionality of feature space (about 32 for faces/fingerprints).
- Depends on the statistical capacity of the intrinsic feature space.
- Realistically bounded by the number of unique humans.
- not more than 40-50 bits.
- Existing approaches quantify security level in the ambient space (e.g., 512-dim) instead of intrinsic space (e.g., 32-dim)
- For privacy schemes, depends on entropy introduced by the privacy-preserving transformation parameters.
- For security schemes, depends on the entropy of the cryptographic scheme/keys.
- Can be made as large as desired.
Important to estimate and report an accurate estimate of the security level.
Characterizing Attacks on Cryptographic BTP Schemes
- Templates can be reconstructed from matching scores or even from binary matching decisions.

- Attacks need access to the decryption keys.
- Once decryption keys are known, the security layer is removed.
- Unsurprising that the templates are no longer secure.
- More accurately characterize such attacks as attacks on key management.
- Standard best practices of key lifecycle management can be employed to protect cryptographic decryption keys.
No cryptographic scheme is secure if the decryption keys are known. No need to demonstrate BTP attacks that effectively ignore this fact.
Next Generation of BTP Methods
Desired BTP Criterion
- Classical BTP criterion: recognition accuracy, irreversibility, renewability/unlinkability
- Modern BTP methods require new criterion to be considered.
- Provable Guarantee: many BTP schemes provide no proof of privacy/security
- Privacy/Security Level: numerically quantified and guaranteed level of protection
- Computational Efficiency: BTP schemes have different computational costs
- Memory/Storage Efficiency: BTP schemes have different memory costs
- Key Management: cryptographic BTP schemes require key management
Comparing Biometric Template Protection Schemes
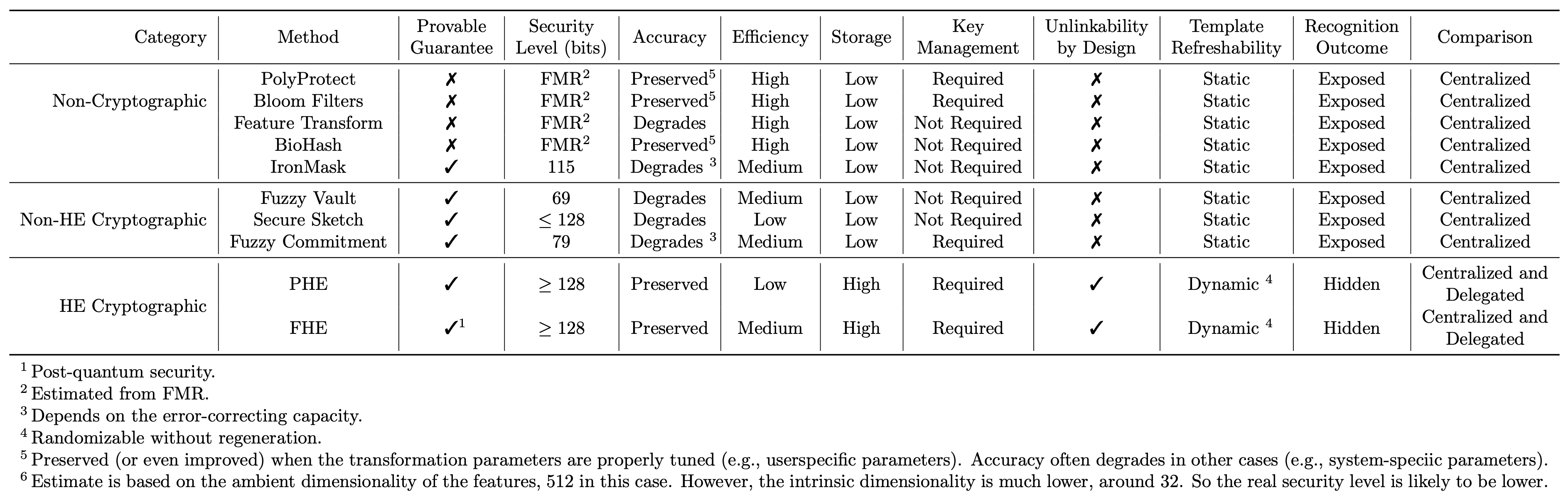
- Vishnu Boddeti, Homomorphic Encryption for Biometric Template Protection, Handbook of Biometric Template Protection: Motivation, Methods and Metrics
Next Generation of BTP Methods
Prior Work: Template Protection
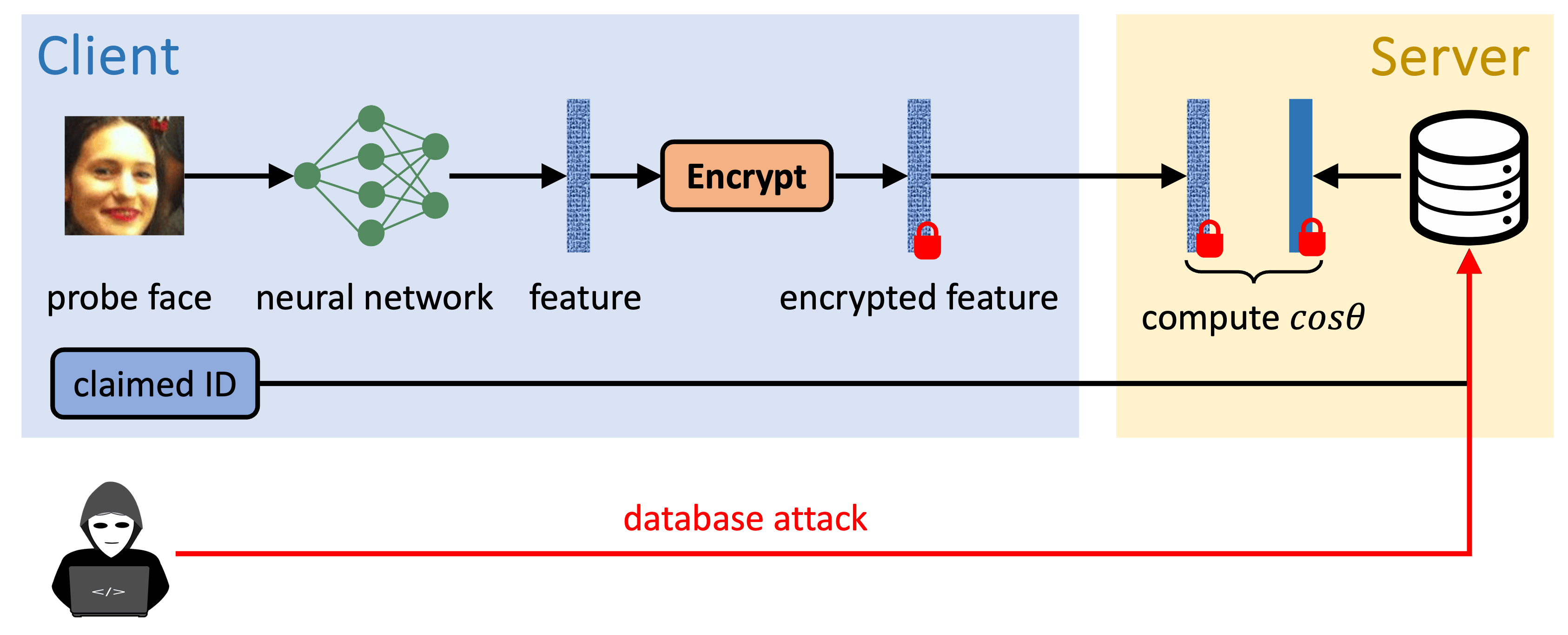
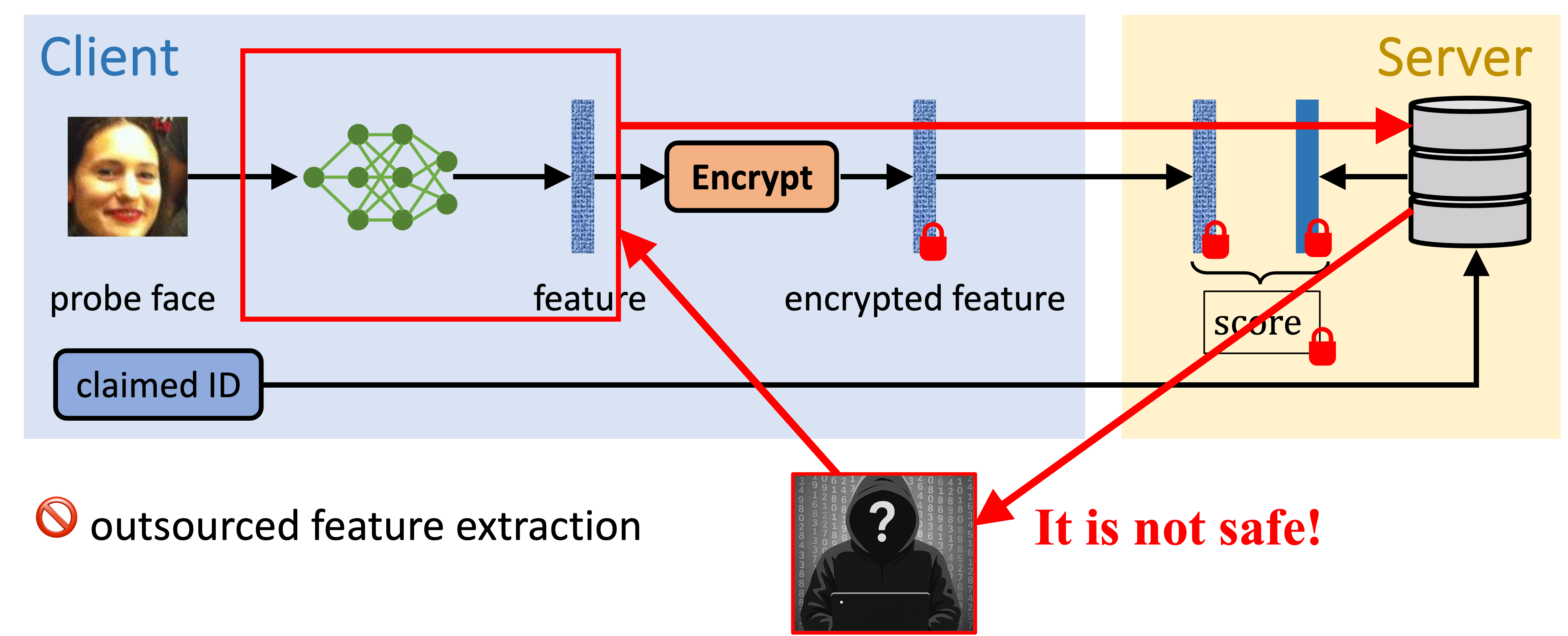
Only Protecting Templates May Not be Safe
 \[
y^* = argmin_{y} D(F(G(y)), t) \quad \hat{x} = G(y^*)
\]
\[
y^* = argmin_{y} D(F(G(y)), t) \quad \hat{x} = G(y^*)
\]
End-to-End Encrypted Face Recognition
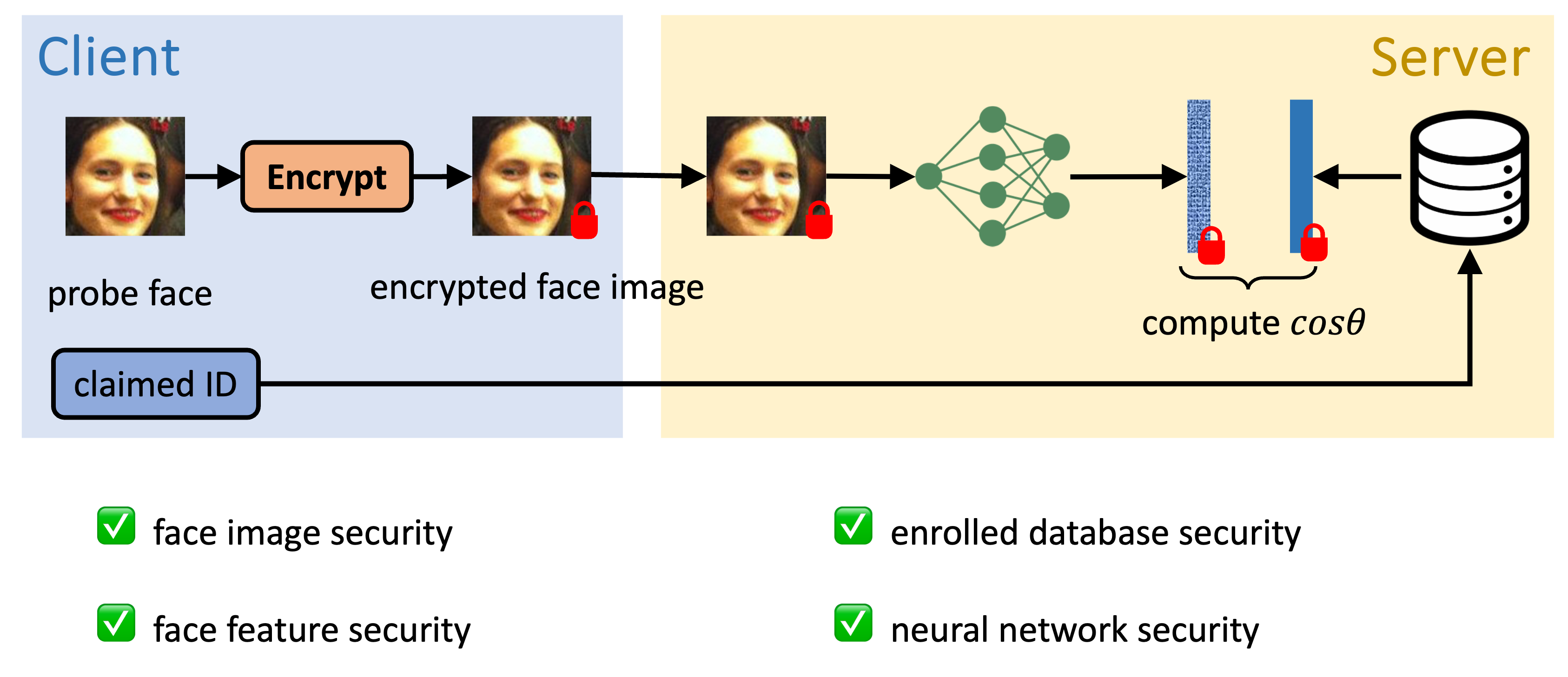
Effectively prevents score or decision-based attacks.
Experiments on Encrypted Face Datasets
Hardware & Software
- Amazon AWS, r5.24xlarge
- 96 CPUs, 768 GB RAM
- Microsoft SEAL, 3.6

| Approach | Backbone | Dataset | Latency(s) | Memory(GB) | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Network | Params | Boot | LFW | AgeDB | CALFW | CPLFW | CFP-FP | Avg | |||
| MPCNN | ResNet32 | 529K | 31 | 97.02 | 83.02 | 87.00 | 78.90 | 82.07 | 85.60 | 7,367 | 286 |
| ResNet44 | 724K | 43 | 98.27 | 87.45 | 90.85 | 83.72 | 87.90 | 89.64 | 9,845 | 286 | |
| AutoFHE1 | ResNet32 | 531K | 8 | 93.53 | 80.88 | 85.40 | 75.67 | 77.96 | 82.69 | 4,001 | 286 |
| CryptoFace | PCNNs | 3.78M | 1 | 98.78 | 92.90 | 93.73 | 83.95 | 87.94 | 91.46 | 1,446 | 277 |
- Architecture searched on CIFAR10.↩
8x speedup from custom neural network design
Next Generation of BTP Methods
Checking integrity of biometric operations under Encryption




We trust BUT we do not verify[BHV+21] Fast and accurate likelihood ratio-based biometric verification secure against malicious adversaries
Commercializing Biometric Security
Concluding Remarks
- Biometric template protection has witnessed tremendous progress over the past 20 years.
- The evolving privacy and security landscape of biometric systems calls for a new generation of BTP methods and beyond to secure biometric systems.
- Potential roadmap for next generation of BTP methods include:
- Prevent conflating privacy and security goals.
- Both privacy and security are important. There is no privacy without security.
- Develop hybrid methods that satisfy both privacy and security.
- Augment classical criterion of BTP methods with those catering to modern challenges.
- Equip cryptographic BTP with correctness verification of encrypted computations.
- Consider biometric systems holistically, and think beyond template protection.
Thank You
